TACACS+ consists of three services: authentication, authorization, and accounting.
Authentication is the action of determining who the user is and whether he or she is allowed access to the switch.
Authorization is the action of determining what the user is allowed to do on the system.
Accounting is the action of collecting data related to resource usage and now
TACACS+ is in the part of the new
CCNA Security certification exam.
Below configuration were created to provide you a basic understanding of
AAA; that of which is commonly used in production networks for authentication, authorization and accounting.
Step 1: Create a backup user account
INHQRL2-3845(config)# dcth privilege 15 password datakrub!
Step 2: Enabling AAA
INHQRL2-3845(config)# aaa new-model
Step 3: Configuring the TACACS+ servers
INHQRL2-3845(config)# tacacs-server host 10.1.50.101 key cisco12345
Step 4: Define the AAA method lists
INHQRL2-3845(config)# aaa authentication login default group tacacs+ local
INHQRL2-3845(config)# aaa authorization exec default group tacacs+ local
Step 5: Enforcing AAA authentication on terminal lines
INHQRL2-3845(config)# line console 0
INHQRL2-3845(config-line)# login authentication default
INHQRL2-3845(config)# line vty 0 15
INHQRL2-3845(config-line)# login authentication default
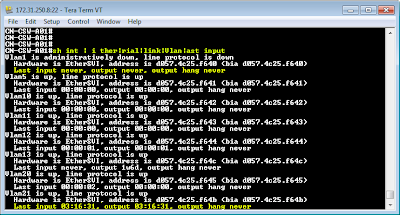
The following snipped are from the TACACS+ authentication configuration on cisco devices.
Example 1: Group tacacs+ enable
!
username dcth privilege 15 password datakrub!
!
enable secret g8:ugvl
!
ip telnet source-interface lo 0
!
line con 0
password dcth!
login local
!
line vty 0 4
password dcth!
login local
!
!
!
aaa new-model
!
aaa authentication login vty group tacacs+ local
aaa authorization exec vty group tacacs+ none
aaa authorization commands 0 vty group tacacs+ local
aaa authorization commands 1 vty group tacacs+ local
aaa authorization commands 7 vty group tacacs+ local
aaa authorization commands 15 vty group tacacs+ local
!
aaa authentication login console group tacacs+ local
aaa authorization exec console group tacacs+ none
aaa authorization commands 1 console group tacacs+ local
aaa authorization commands 7 console group tacacs+ local
aaa authorization commands 15 console group tacacs+ local
!
aaa authentication enable default group tacacs+ enable
!
aaa accounting exec vty start-stop group tacacs+
aaa accounting commands 1 vty start-stop group tacacs+
aaa accounting commands 7 vty start-stop group tacacs+
aaa accounting commands 15 vty start-stop group tacacs+
aaa accounting exec console start-stop group tacacs+
aaa accounting commands 1 console start-stop group tacacs+
aaa accounting commands 7 console start-stop group tacacs+
aaa accounting commands 15 console start-stop group tacacs+
!
aaa authorization console
aaa authorization config-commands
!
!
!
ip tacacs source-interface Loopback 0
!
!
tacacs-server host 10.1.50.101
tacacs-server key cisco12345
!
!
!
!
!
line con 0
authorization exec console
authorization command 1 console
authorization command 7 console
authorization command 15 console
accounting commands 1 console
accounting commands 7 console
accounting commands 15 console
accounting exec console
logging synchronous
login authentication console
line vty 0 4
authorization commands 1 vty
authorization commands 7 vty
authorization commands 15 vty
authorization exec vty
accounting commands 1 vty
accounting commands 7 vty
accounting commands 15 vty
accounting exec vty
logging synchronous
login authentication vty
!
!
Example 2: ACS group tacacs+ and RADIUS-LOGIN group enable
!
enable secret 5 $1$azKE$exucFBdjapkq2aspUIS7M0
!
aaa new-model
!
aaa authentication login ACS group tacacs+ enable
aaa authentication login RADIUS-LOGIN group radius
aaa authentication enable default group tacacs+ enable
aaa authentication ppp RADIUS-LOGIN group radius
aaa authorization console
aaa authorization config-commands
aaa authorization exec ACS group tacacs+ if-authenticated
aaa authorization commands 0 ACS group tacacs+ if-authenticated
aaa authorization commands 1 ACS group tacacs+ if-authenticated
aaa authorization commands 15 ACS group tacacs+ if-authenticated
aaa accounting update newinfo
aaa accounting exec ACS start-stop group tacacs+
aaa accounting commands 0 ACS start-stop group tacacs+
aaa accounting commands 1 ACS start-stop group tacacs+
aaa accounting commands 15 ACS start-stop group tacacs+
aaa accounting connection ACS start-stop group tacacs+
!
ip ssh source-interface Loopback0
!
ip tacacs source-interface Loopback0
!
access-list 20 permit 156.32.0.0 0.1.255.255
access-list 20 permit 156.34.0.0 0.7.255.255
access-list 20 permit 156.42.0.0 0.7.255.255
access-list 20 permit 156.50.0.0 0.3.255.255
access-list 20 permit 156.54.0.0 0.1.255.255
access-list 20 permit 156.56.0.0 0.0.255.255
access-list 20 permit 146.171.0.0 0.0.255.255
access-list 20 permit 149.65.0.0 0.0.255.255
access-list 20 permit 189.103.13.0 0.0.0.255
access-list 20 permit 156.52.71.192 0.0.0.63
access-list 20 permit 156.52.9.192 0.0.0.63
access-list 20 deny any log
!
!
tacacs-server host 156.52.197.26
tacacs-server host 156.52.8.16
tacacs-server timeout 10
tacacs-server directed-request
tacacs-server key 7 06031D344F4B1GG606041B08
!
!
line con 0
access-class 20 in
timeout login response 15
password 7 040A3757062A1F7459160B1956035C57
logging synchronous
transport preferred none
stopbits 1
line vty 0 4
access-class 20 in
timeout login response 15
password 7 124839461B005F3E7A242A26773D7240
logging synchronous
transport preferred none
transport input telnet
!
!
**********************************************************************************************
WARNING TO UNAUTHORIZED USERS:
This system is for use by authorized users only. Any individual using this system,
by such use, acknowledges and consents to the right of the company to monitor,
access, use, and disclose anyinformation generated, received, or stored on the
systems, and waives any right of privacy or expectation of privacy on the part of
that individual in connection with his or her use of this system.
**********************************************************************************************
Username:
boylaser
Enter PASSCODE:
*
You could now configure TACACS+ server for system authentication