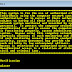
This should give you an idea of how SNMPv3 works and how to configure it on your Cisco devices.
SNMP Concepts
SNMP is a protocol that operates at the application layer; it uses the default UDP port 161 for general SNMP messages and UDP port 162 for SNMP trap messages and it defines a method of communication between various networking devices and a central manager for use with the monitoring and management of these devices.
SNMP Versions
There are three different versions of SNMP that can be configured:
I created username nagios password stal1148 on the network device (130.30.230.1) for test SNMP V3 on the Nagios monitoring system.
Here is an example using SNMP version 3:
CC-CSW-A01(config)#snmp-server group cisconetwork v3 ?
auth group using the authNoPriv Security Level
noauth group using the noAuthNoPriv Security Level
priv group using SNMPv3 authPriv security level
CC-CSW-A01(config)#snmp-server group cisconetwork v3 pri
CC-CSW-A01(config)#snmp-server group cisconetwork v3 priv ?
access specify an access-list associated with this group
context specify a context to associate these views for the group
match context name match criteria
notify specify a notify view for the group
read specify a read view for the group
write specify a write view for the group
<cr>
CC-CSW-A01(config)#snmp-server group cisconetwork v3 priv ?
access specify an access-list associated with this group
context specify a context to associate these views for the group
match context name match criteria
notify specify a notify view for the group
read specify a read view for the group
write specify a write view for the group
<cr>
Verifying SNMP Version 3:
Perform this task to verify the SNMPv3 configuration. The show commands can be entered in any order.
CC-CSW-A01#show running-config | incl snmp
CC-CSW-A01#show snmp group
CC-CSW-A01#show snmp user
CC-CSW-A01#show snmp engineID
CC-CSW-A01#show snmp sessions
CC-CSW-A01#show snmp trap
To test from the CLI on the Nagios monitoring system :
Test Monitor CPU:
[root@NAGIOS libexec]# ./check_snmp_load.pl -v -H 130.30.230.1 -l nagios -x stal1148 -T splat -w 95 -c 100
Alarm at 60 + 5
SNMPv3 login
SNMPv3 AuthNoPriv login : nagios, md5
Checking OID : 1.3.6.1.4.1.2620.1.6.7.2.2.0
OID returned 0
CPU used 0.0% (<95) : OK .........
Test Monitor Disk Space:
[root@FRNAGIOS libexec]# ./check_snmp_storage.pl -v -H 130.30.230.1 -l nagios -x stal1148 -m / -w 80 -c 90
Alarm at 60
SNMPv3 login
SNMPv3 AuthNoPriv login : nagios, md5
Filter : /
OID : 1.3.6.1.2.1.25.2.3.1.3.102, Desc : Swap Space
OID : 1.3.6.1.2.1.25.2.3.1.3.3, Desc : /opt
Name : /opt, Index : 3
OID : 1.3.6.1.2.1.25.2.3.1.3.101, Desc : Real Memory .........
Test Monitor Interface:
[root@NAGIOS libexec]# ./check_snmp_int.pl -v -H 130.30.230.1 -l nagios -x stal1148 -n eth1 -k -w 0,0 -c 0,0 -B -r -t 60
Alarm at 60 + 5
SNMPv3 AuthNoPriv login : nagios, md5
Filter : eth1
OID : 1.3.6.1.2.1.2.2.1.2.1, Desc : lo
OID : 1.3.6.1.2.1.2.2.1.2.14, Desc : eth13
OID : 1.3.6.1.2.1.2.2.1.2.20, Desc : eth11.2054 .........
Configuring SNMPv3 versus SNMPv2c is highly recommended due the increased security capabilities. Now stop using the insecure SNMPv1 and SNMPv2c on your production networks!
SNMP is a protocol that operates at the application layer; it uses the default UDP port 161 for general SNMP messages and UDP port 162 for SNMP trap messages and it defines a method of communication between various networking devices and a central manager for use with the monitoring and management of these devices.
SNMP Versions
There are three different versions of SNMP that can be configured:
- SNMPv1 - This was the original version of SNMP; SNMPv1 utilizes a community based security mechanism.
- SNMPv2c - This was created to update a number of little things within SNMPv1; SNMPv2c utilizes a community based security mechanism.
- SNMPv3 - This was developed to provide a much higher level of security then was provided by either previous version. A couple different security features are implemented within the SNMPv3 standard; these include:
- Message integrity
- Authentication
- Encryption
I created username nagios password stal1148 on the network device (130.30.230.1) for test SNMP V3 on the Nagios monitoring system.
CC-CSW-A01(config)#snmp-server group cisconetwork v3 ?
auth group using the authNoPriv Security Level
noauth group using the noAuthNoPriv Security Level
priv group using SNMPv3 authPriv security level
CC-CSW-A01(config)#snmp-server group cisconetwork v3 pri
CC-CSW-A01(config)#snmp-server group cisconetwork v3 priv ?
access specify an access-list associated with this group
context specify a context to associate these views for the group
match context name match criteria
notify specify a notify view for the group
read specify a read view for the group
write specify a write view for the group
<cr>
CC-CSW-A01(config)#snmp-server group cisconetwork v3 priv ?
access specify an access-list associated with this group
context specify a context to associate these views for the group
match context name match criteria
notify specify a notify view for the group
read specify a read view for the group
write specify a write view for the group
<cr>
Verifying SNMP Version 3:
Perform this task to verify the SNMPv3 configuration. The show commands can be entered in any order.
CC-CSW-A01#show running-config | incl snmp
CC-CSW-A01#show snmp group
CC-CSW-A01#show snmp user
CC-CSW-A01#show snmp engineID
CC-CSW-A01#show snmp sessions
CC-CSW-A01#show snmp trap
To test from the CLI on the Nagios monitoring system :
Test Monitor CPU:
[root@NAGIOS libexec]# ./check_snmp_load.pl -v -H 130.30.230.1 -l nagios -x stal1148 -T splat -w 95 -c 100
Alarm at 60 + 5
SNMPv3 login
SNMPv3 AuthNoPriv login : nagios, md5
Checking OID : 1.3.6.1.4.1.2620.1.6.7.2.2.0
OID returned 0
CPU used 0.0% (<95) : OK .........
Test Monitor Disk Space:
[root@FRNAGIOS libexec]# ./check_snmp_storage.pl -v -H 130.30.230.1 -l nagios -x stal1148 -m / -w 80 -c 90
Alarm at 60
SNMPv3 login
SNMPv3 AuthNoPriv login : nagios, md5
Filter : /
OID : 1.3.6.1.2.1.25.2.3.1.3.102, Desc : Swap Space
OID : 1.3.6.1.2.1.25.2.3.1.3.3, Desc : /opt
Name : /opt, Index : 3
OID : 1.3.6.1.2.1.25.2.3.1.3.101, Desc : Real Memory .........
Test Monitor Interface:
[root@NAGIOS libexec]# ./check_snmp_int.pl -v -H 130.30.230.1 -l nagios -x stal1148 -n eth1 -k -w 0,0 -c 0,0 -B -r -t 60
Alarm at 60 + 5
SNMPv3 AuthNoPriv login : nagios, md5
Filter : eth1
OID : 1.3.6.1.2.1.2.2.1.2.1, Desc : lo
OID : 1.3.6.1.2.1.2.2.1.2.14, Desc : eth13
OID : 1.3.6.1.2.1.2.2.1.2.20, Desc : eth11.2054 .........
Configuring SNMPv3 versus SNMPv2c is highly recommended due the increased security capabilities. Now stop using the insecure SNMPv1 and SNMPv2c on your production networks!