Figure 1: IOS Version Required
Figure 2: Cisco 3560, 3750, 4500, 6500 802.1x Configuration
Figure 3: Cisco 3560, 2750, 4500, 6500 802.1x Configuration Removal
1. Introduction
The objective of this content is to provide an overview of the 802.1x capability of the Cisco IOS Switches. This allows stakeholders to determine whether port-based authentication using 802.1x is a viable option for their specific scenario as well as how the technology works to keep resources secure.
This content is designed to provide network engineers with the skills and knowledge to effectively deploy and troubleshoot network based authentication using 802.1x. Configuration examples are provided to assist the engineer in adding 802.1x port security to the Cisco devices. Known issues and questions are addressed to help educate users and engineers that
802.1x Features
The 802.1x feature will secure physical network ports or wireless connections by requiring valid authentication. 802.1x is a way to make sure a user is who they say they are by checking their credentials against an authentication server.
This server can be designed specifically for authenticating users on the network, or can have multi-purposes such as Active Directory authentication or Radius Servers being used for authentication other than networking.
802.1x uses a supplicant (user), authenticator (switch or access point), and an authentication server (Radius Server). The supplicant notifies the authenticator that it would like to be authenticated. Once the authenticator receives this request, it will forward this information to the authentication server for validation. This information can be in many forms including username/password, machine based certificate, or smart badge based certificate. These credentials will be checked against the server in order to allow the supplicant access to the authenticator. Once access is granted to the supplicant, the user is able to make use of the network resources. If a supplicant is not authorized, the network administrator can determine the access level that is granted. An unauthorized supplicant can be denied any service on the network, placed into a quarantine network, or into an “Internet-only” vlan. Administrators have complete control placement of an unauthorized supplicant.
2. Direction
Company has many sites in which 3rd Party collaboration takes place. 802.1x is one method of securing a network that could possibly be accessed by unauthorized users. By requiring authentication credentials, a network connection can be locked down protecting corporate resources that would otherwise be available on an unsecured connection.
Smart Badge capability was initially chosen as the authentication that would be used as it has been deployed globally. All machines have the same image using the Global Information Link 3 () configuration. Using Smart Badge based certificates has proven to be an obstacle due to the need of a user to input a PIN. An alternative to using a Smart Badge based certificate is to use a machine based certificate placed on each laptop or workstation. This machine certificate allows a device to be placed on the Company network without user intervention. Devices not containing the machine certificate are not allowed Company network access. Access to the device and Companys’ network will continue to require Smartbadge authentication – restricting unauthorized users from taking an unattended Company authenticated device and placing them on the network.
The EAP type was chosen as EAP-TLS that uses certificates on the Smart Badge. The EAP-TLS protocol is used by the Steel-Belted Radius, which is currently the Company Wireless LAN authentication server.
Requirements
Connecting Device: Any device connecting to the switch port should be able to perform EAP authentication. This functionality is provided by an EAP supplicant. The computers have a native Microsoft EAP supplicant that needs to be enabled. A GOP package has been created to enable the EAP supplicant on the computers.
The authentication of the EAP enabled computers has been tested and is working fine.
Non-EAP devices such as printers and other peripherals will authenticate using their MAC address. The Network Assets team is presently working on the backend MAC based authentication infrastructure for non-EAP enabled devices.
The Cisco IP Phones have an EAP supplicant, version 8.5.2 of the IP phone load. Network Assets team is presently working on testing the new IP phone image. The Network Assets team is planning to conduct testing on the 6500, 4500, 3K & 2K switches.
Switches that have been tested working with 802.1x include Cisco 3750, 3560, 4500, and 6500 series Catalyst Switches.
802.1x has been tested using specific versions of IOS. A list of required versions to be used can be seen below in table 1. In most cases, any version higher than what is listed will suffice as a requirement.
3. Configuration
Cisco 3560, 3750, 4500, 6500 Configuration and Troubleshooting
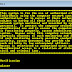
Adding Configuration 802.1x has three parts to the configuration.
1. 802.1x Global Configuration
2. Radius Server Authentication
3. nterface Configuration
802.1x-Switch(config)# dot1x system-auth-control
(***Radius Server Authentication Global Configuration***)
802.1x-Switch(config)# radius-server host 146.23.102.28 auth-port 1645
acct-port 1646
802.1x-Switch(config)# radius-server key 7 011B09110A5D561C2D1F
(***Interface Configuration***)
802.1x-Switch(config)# interface GigabitEthernet0/1
802.1x-Switch(config-if)# dot1x pae authenticator
802.1x-Switch(config-if)# dot1x port-control auto
802.1x-Switch(config-if)# dot1x violation-mode protect
Removing Configuration
If 802.1x requires removal from an interface, only the interface needs to be changed (See figure 2). The global configuration for 802.1x and Radius Server authentication can remain on the switch.
(***Removing 802.1x Interface Configuration***)
802.1x-Switch(config)# interface GigabitEthernet5/27
802.1x-Switch(config-if)# no authentication port-control auto
802.1x-Switch(config-if)# no authentication violation restrict
802.1x-Switch(config-if)# no dot1x pae authenticator
References: Introduction to IEEE 802.1x and Cisco Identity-Based Networking Services
Figure 2: Cisco 3560, 3750, 4500, 6500 802.1x Configuration
Figure 3: Cisco 3560, 2750, 4500, 6500 802.1x Configuration Removal
1. Introduction
The objective of this content is to provide an overview of the 802.1x capability of the Cisco IOS Switches. This allows stakeholders to determine whether port-based authentication using 802.1x is a viable option for their specific scenario as well as how the technology works to keep resources secure.
This content is designed to provide network engineers with the skills and knowledge to effectively deploy and troubleshoot network based authentication using 802.1x. Configuration examples are provided to assist the engineer in adding 802.1x port security to the Cisco devices. Known issues and questions are addressed to help educate users and engineers that
802.1x Features
The 802.1x feature will secure physical network ports or wireless connections by requiring valid authentication. 802.1x is a way to make sure a user is who they say they are by checking their credentials against an authentication server.
802.1x uses a supplicant (user), authenticator (switch or access point), and an authentication server (Radius Server). The supplicant notifies the authenticator that it would like to be authenticated. Once the authenticator receives this request, it will forward this information to the authentication server for validation. This information can be in many forms including username/password, machine based certificate, or smart badge based certificate. These credentials will be checked against the server in order to allow the supplicant access to the authenticator. Once access is granted to the supplicant, the user is able to make use of the network resources. If a supplicant is not authorized, the network administrator can determine the access level that is granted. An unauthorized supplicant can be denied any service on the network, placed into a quarantine network, or into an “Internet-only” vlan. Administrators have complete control placement of an unauthorized supplicant.
2. Direction
Company has many sites in which 3rd Party collaboration takes place. 802.1x is one method of securing a network that could possibly be accessed by unauthorized users. By requiring authentication credentials, a network connection can be locked down protecting corporate resources that would otherwise be available on an unsecured connection.
Smart Badge capability was initially chosen as the authentication that would be used as it has been deployed globally. All machines have the same image using the Global Information Link 3 () configuration. Using Smart Badge based certificates has proven to be an obstacle due to the need of a user to input a PIN. An alternative to using a Smart Badge based certificate is to use a machine based certificate placed on each laptop or workstation. This machine certificate allows a device to be placed on the Company network without user intervention. Devices not containing the machine certificate are not allowed Company network access. Access to the device and Companys’ network will continue to require Smartbadge authentication – restricting unauthorized users from taking an unattended Company authenticated device and placing them on the network.
The EAP type was chosen as EAP-TLS that uses certificates on the Smart Badge. The EAP-TLS protocol is used by the Steel-Belted Radius, which is currently the Company Wireless LAN authentication server.
Requirements
Connecting Device: Any device connecting to the switch port should be able to perform EAP authentication. This functionality is provided by an EAP supplicant. The computers have a native Microsoft EAP supplicant that needs to be enabled. A GOP package has been created to enable the EAP supplicant on the computers.
The authentication of the EAP enabled computers has been tested and is working fine.
Non-EAP devices such as printers and other peripherals will authenticate using their MAC address. The Network Assets team is presently working on the backend MAC based authentication infrastructure for non-EAP enabled devices.
The Cisco IP Phones have an EAP supplicant, version 8.5.2 of the IP phone load. Network Assets team is presently working on testing the new IP phone image. The Network Assets team is planning to conduct testing on the 6500, 4500, 3K & 2K switches.
Switches that have been tested working with 802.1x include Cisco 3750, 3560, 4500, and 6500 series Catalyst Switches.
802.1x has been tested using specific versions of IOS. A list of required versions to be used can be seen below in table 1. In most cases, any version higher than what is listed will suffice as a requirement.
Switch
|
IOS Version
|
3560
| |
3750
|
12.2(53)SE
|
4500
|
12.2(53)SG1
|
6500
|
12.2(33)SXI
|
Cisco 3560, 3750, 4500, 6500 Configuration and Troubleshooting
Adding Configuration 802.1x has three parts to the configuration.
1. 802.1x Global Configuration
2. Radius Server Authentication
3. nterface Configuration
Configuration is detailed in figure 1.
(***802.1x Global Configuration***)
802.1x-Switch(config)# aaa authentication dot1x default group radius802.1x-Switch(config)# dot1x system-auth-control
(***Radius Server Authentication Global Configuration***)
802.1x-Switch(config)# radius-server host 146.23.102.28 auth-port 1645
acct-port 1646
802.1x-Switch(config)# radius-server key 7 011B09110A5D561C2D1F
(***Interface Configuration***)
802.1x-Switch(config)# interface GigabitEthernet0/1
802.1x-Switch(config-if)# dot1x pae authenticator
802.1x-Switch(config-if)# dot1x port-control auto
802.1x-Switch(config-if)# dot1x violation-mode protect
Figure 2: Cisco 3560, 3750, 4500, 6500 802.1x Configuration
Removing Configuration
If 802.1x requires removal from an interface, only the interface needs to be changed (See figure 2). The global configuration for 802.1x and Radius Server authentication can remain on the switch.
(***Removing 802.1x Interface Configuration***)
802.1x-Switch(config)# interface GigabitEthernet5/27
802.1x-Switch(config-if)# no authentication port-control auto
802.1x-Switch(config-if)# no authentication violation restrict
802.1x-Switch(config-if)# no dot1x pae authenticator
Figure 3: Cisco 3560, 3750, 4500, 6500 802.1x Configuration Removal















0 comments:
Post a Comment