This article will show how to use Policy-Based Routing to different default routes are used based on the source of the ip address. Let me show you the diagram and the configuration step. The example below should cover basic route-map configuration.
Create a simple ACL:
SGHQSL1-4506(config)#ip access-list extended WVIP
SGHQSL1-4506(config-ext-nacl)# permit ip host 146.30.50.31 any
SGHQSL1-4506(config-ext-nacl)# permit ip host 146.30.50.32 any
SGHQSL1-4506(config)#ip access-list extended WVISITOR
SGHQSL1-4506(config-ext-nacl)# permit ip 146.31.50.65 any
Step 2 - Creating a route-map
To create a route-map, go into route-map configuration mode, like this:
SGHQSL1-4506(config)#route-map InternetWVISITOR permit 5
SGHQSL1-4506(config-route-map) #match ip address WVISITOR
SGHQSL1-4506(config-route-map) #set ip next-hop 146.10.50.15
SGHQSL1-4506(config)#route-map InternetWVIP permit 10
SGHQSL1-4506(config-route-map) #match ip address WVIP
SGHQSL1-4506(config-route-map) #set ip next-hop 146.10.50.12
In this example, this will match all the traffic permitted through access-list WVIP change the next-hop to 146.10.050.12 and all the traffice permitted through access-list WVISITOR change the next-hop to 146.10.50.15
Step 3 - Applying the route-map to the interface
Next, you need to apply this policy/route-map to the interface where the traffic is coming in.
SGHQSL1-4506(config)#interface Vlan30
SGHQSL1-4506(config-if)#ip policy route-map InternetWVIP
SGHQSL1-4506(config)#interface Vlan31
SGHQSL1-4506(config-if)#ip policy route-map InternetWVISITOR
Some helpful commands to monitor and verify the access list, route-map and ip policy.
SGHQSL1-4506#sh ip policy
Interface Route map
Vlan30 InternetWVIP
Vlan31 InternetWVISITOR
SGHQSL1-4506#sh route-map
route-map InternetWVIP, permit, sequence 10
Match clauses:
ip address (access-lists): VIP
Set clauses:
ip next-hop 146.10.50.12
Policy routing matches: 17846460 packets, 2246593826 bytes
route-map InternetWVISITOR, permit, sequence 10
Match clauses:
ip address (access-lists): wlan
Set clauses:
ip next-hop 146.10.50.15
Policy routing matches: 2450155 packets, 322873006 bytes
SGHQSL1-4506#sh access-lists WVIP
Extended IP access list WVIP
10 permit ip host 146.30.50.31 any
20 permit ip host 146.30.50.32 any (278 matches)
SGHQSL1-4506#sh access-lists WVISITOR
Extended IP access list WVISITOR
10 permit ip 146.31.50.65 0.0.0.255 any (2470017 matches)
Note: The traffic that does not match the policy uses the default route configured in the core switch.
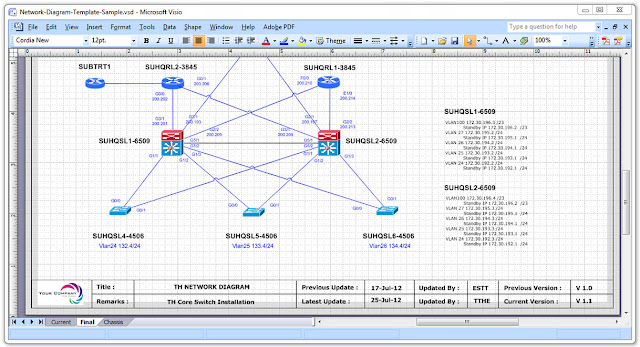
The previous diagram illustrates the structure of Route Map and Policy-Based Routing
IP Address Assignment:- VLAN 10 Management Vlan IP address: 146.10.50.xx/24
- VLAN 20 Server Vlan IP address: 146.20.50.xx/24
- VLAN 30 Wireless Lan VIP IP address: 146.30.50.xx/24
- VLAN 31 Wireless Lan Visitor IP address: 146.30.50.xx/24
- VLAN 40 Workstation Vlan IP address: 146.40.50.xx/24
Create a simple ACL:
SGHQSL1-4506(config)#ip access-list extended WVIP
SGHQSL1-4506(config-ext-nacl)# permit ip host 146.30.50.31 any
SGHQSL1-4506(config-ext-nacl)# permit ip host 146.30.50.32 any
SGHQSL1-4506(config)#ip access-list extended WVISITOR
SGHQSL1-4506(config-ext-nacl)# permit ip 146.31.50.65 any
Step 2 - Creating a route-map
To create a route-map, go into route-map configuration mode, like this:
SGHQSL1-4506(config)#route-map InternetWVISITOR permit 5
SGHQSL1-4506(config-route-map) #match ip address WVISITOR
SGHQSL1-4506(config-route-map) #set ip next-hop 146.10.50.15
SGHQSL1-4506(config)#route-map InternetWVIP permit 10
SGHQSL1-4506(config-route-map) #match ip address WVIP
SGHQSL1-4506(config-route-map) #set ip next-hop 146.10.50.12
In this example, this will match all the traffic permitted through access-list WVIP change the next-hop to 146.10.050.12 and all the traffice permitted through access-list WVISITOR change the next-hop to 146.10.50.15
Step 3 - Applying the route-map to the interface
Next, you need to apply this policy/route-map to the interface where the traffic is coming in.
SGHQSL1-4506(config)#interface Vlan30
SGHQSL1-4506(config-if)#ip policy route-map InternetWVIP
SGHQSL1-4506(config)#interface Vlan31
SGHQSL1-4506(config-if)#ip policy route-map InternetWVISITOR
Some helpful commands to monitor and verify the access list, route-map and ip policy.
SGHQSL1-4506#sh ip policy
Interface Route map
Vlan30 InternetWVIP
Vlan31 InternetWVISITOR
route-map InternetWVIP, permit, sequence 10
Match clauses:
ip address (access-lists): VIP
Set clauses:
ip next-hop 146.10.50.12
Policy routing matches: 17846460 packets, 2246593826 bytes
route-map InternetWVISITOR, permit, sequence 10
Match clauses:
ip address (access-lists): wlan
Set clauses:
ip next-hop 146.10.50.15
Policy routing matches: 2450155 packets, 322873006 bytes
SGHQSL1-4506#sh access-lists WVIP
Extended IP access list WVIP
10 permit ip host 146.30.50.31 any
20 permit ip host 146.30.50.32 any (278 matches)
SGHQSL1-4506#sh access-lists WVISITOR
Extended IP access list WVISITOR
10 permit ip 146.31.50.65 0.0.0.255 any (2470017 matches)
Note: The traffic that does not match the policy uses the default route configured in the core switch.